Powerful Guide to Public and Private Key Cryptography. In today’s digital-first world, securing communication is no longer optional—it’s a necessity. Whether you’re sending a private email, transferring cryptocurrency, or accessing your bank account online, encryption plays a critical role in keeping your data safe. This Powerful Guide to Public and Private Key Cryptography will help you understand how these keys work, why they matter, and how they are used in real-world applications.
What is Cryptography?
Cryptography is the science of protecting information by transforming it into an unreadable format for anyone who doesn’t have the proper authorization. The process involves algorithms, keys, and protocols to ensure confidentiality, integrity, and authenticity of data.
The Powerful Guide to Public and Private Key Cryptography focuses on the two most important forms of key-based encryption—public key and private key systems.
Understanding Public and Private Key Cryptography
Public and private key cryptography, also known as asymmetric cryptography, is a method where two keys are used—one for encryption and another for decryption. The Powerful Guide to Public and Private Key Cryptography explains it in simple terms:
- Public Key: Can be shared with anyone; used for encryption.
- Private Key: Must be kept secret; used for decryption.
When someone wants to send you secure data, they use your public key to encrypt it. Only your private key can decrypt it, ensuring that the message stays confidential.
How It Works – Step by Step

In the Powerful Guide to Public and Private Key Cryptography, here’s how the process unfolds:
- Key Generation – A user generates a pair of keys: one public, one private.
- Public Key Sharing – The public key is distributed openly, even over insecure channels.
- Encryption – The sender uses the public key to encrypt data.
- Decryption – The recipient uses their private key to decrypt the data.
- Authentication – Digital signatures verify the sender’s identity.
Benefits of Public and Private Key Cryptography
The Powerful Guide to Public and Private Key Cryptography highlights the many benefits of this system:
- Enhanced Security: Even if the public key is intercepted, the data remains secure.
- Authentication: Ensures the data sender is genuine.
- Non-repudiation: Prevents the sender from denying the authenticity of the message.
- Scalability: Works well in large, distributed systems.
Public Key Cryptography in Action
You may not realize it, but the Powerful Guide to Public and Private Key Cryptography is applied in many of your daily activities:
- Email Encryption: Using tools like PGP (Pretty Good Privacy).
- Website Security: SSL/TLS certificates use public and private keys.
- Cryptocurrency Transactions: Blockchain wallets rely on key pairs.
- Digital Signatures: Used in legal documents and software verification.
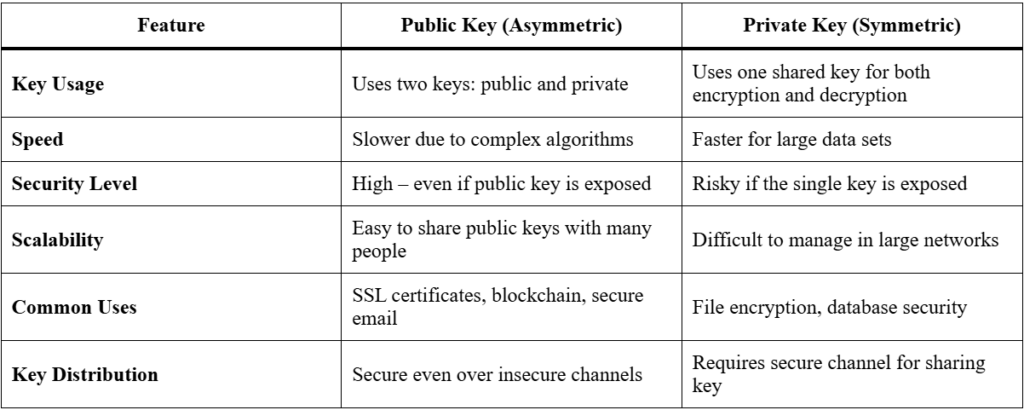
Comparison: Public vs Private Key Cryptography
The Powerful Guide to Public and Private Key Cryptography wouldn’t be complete without a direct comparison of the two approaches.
Why Public and Private Key Cryptography is More Relevant Today
With cyber threats on the rise, the Powerful Guide to Public and Private Key Cryptography stresses the importance of adopting encryption practices in all online interactions. From online shopping to remote work security, using key-based encryption is the backbone of trust on the internet.
How Public and Private Key Cryptography Enhances Privacy
The Powerful Guide to Public and Private Key Cryptography emphasizes privacy as a fundamental human right. With asymmetric cryptography:
- Your private messages stay private.
- Hackers can’t decode your data without the private key.
- Personal information is safe from identity theft.
Challenges in Using Public and Private Key Cryptography
While the Powerful Guide to Public and Private Key Cryptography praises its strengths, there are also some challenges:
- Processing Speed: Public key encryption can be slower than symmetric methods.
- Key Management: Losing your private key means losing access to encrypted data.
- Complexity: Requires technical knowledge for proper implementation.
Future of Public and Private Key Cryptography
The Powerful Guide to Public and Private Key Cryptography predicts advancements with quantum-resistant algorithms and biometric authentication to enhance security. As technology evolves, so will encryption methods, ensuring stronger protection against cyber threats.
Best Practices for Using Public and Private Key Cryptography
Here’s what the Powerful Guide to Public and Private Key Cryptography recommends:
- Keep Your Private Key Secure – Store it offline if possible.
- Use Strong Key Lengths – Minimum 2048 bits for RSA.
- Regularly Update Keys – To prevent vulnerabilities.
- Implement Multi-Factor Authentication – Adds extra layers of security.
- Educate Your Team – Awareness is as important as technology.
Common Myths About Public and Private Key Cryptography
The Powerful Guide to Public and Private Key Cryptography helps debunk a few myths:
- Myth 1: Public key encryption is unbreakable.
Truth: It’s extremely secure but not immune to future quantum computing threats. - Myth 2: Only tech experts can use it.
Truth: User-friendly tools make encryption accessible to everyone. - Myth 3: It’s too slow for real-world applications.
Truth: Modern hardware makes encryption fast enough for daily use.
Conclusion
The Powerful Guide to Public and Private Key Cryptography offers more than just technical details it provides a roadmap for securing your online life. By understanding and implementing key-based encryption, you protect your privacy, secure sensitive data, and build trust in the digital space.
As cyber threats continue to grow, this Powerful Guide to Public and Private Key Cryptography reminds us that encryption is not just for businesses it’s for everyone. Whether you’re a casual internet user or a tech professional, mastering public and private key cryptography is an investment in your digital safety.

I’m a passionate content writer who loves crafting clear, engaging, and user friendly content that connects with readers. From blog articles to web copy, I create words that inform, inspire, and leave a lasting impact










